What is spy software
Contents:
These options can be turned off in the Smartphone Interface. Online Control Panel This is where you login to your account to see the logged results insert by the phone. Accessible from any computer or phone web browser. This high-tech monitoring software will allow you to see exactly what they do while you are away. Are your kids texting while driving or using the phone in all hours of the night? Are your employees sending company property? Do they erase their phone logs? That won't matter because the software does not rely on the phone's internal logging system.
This powerful system gives you the ability to monitor activities online in real time. Your logs are safely stored in your secure Mobile Spy account which is accessible from any web browser using your username and password. You can login anytime from any location to view results without needing access to the device. The activities logged are each described below. All logs can be easily exported to CSV! Unlike anything ever seen in the mobile software industry, this innovation allows you to securely perform LIVE monitoring and control on your smartphone from anywhere.
Categories
If you choose to purchase the premium app, you can view the device's screen like a television along with a map of the current location instantly. Need the ability to have logs sent to your email? You can have selected logs sent at any interval you choose, such as hourly or daily. Lock the Device Lock and unlock the device with an optional siren alarm. Do you need to know if your child is sending and receiving text messages that may be inappropriate or cause them to get into trouble? One of the fears for today's parents is that their child may be using the mobile phone for sexting.
- How Does Cell Phone Spy Software Work?.
- track a person by cell phone.
- spyphone download android!
Sexting is a term that describes text messages that contain explicit language of a sexual nature. Children will be curious about the new information that they are exposed to and might plan to engage in sexual activities. And because of their inexperience, children do not understand the consequences of their actions. How much time does your child or employee spend making phone calls with your mobile phone?
Who are they calling and when? With Mobile Spy smartphone monitoring software you can monitor their phone call information. Find out who they call, when they call, and how much time they spend on each call. Other mobile monitoring software will only give you URLs visited on the default browser and text messages from the app that came with the phone. Mobile Spy has extra features that monitor social media messenger apps such as Facebook, Twitter and WhatsApp. Now you get a better picture of all the communication channels your children or employees use.
One reason why Gmail is so popular is because it is so easy to set up. So easy that your kids may be more inclined to get a Gmail address.
Top 10 Spy Software – Best Spy Apps Reviews
The Gmail logging feature will log all the details of incoming and outgoing Gmails. As a parent you have concerns about who your child is contacting with her mobile phone.
By definition, cell phone spy software refers to any software program which allows you to monitor the use of a cell phone in some way. Different people may call. I'm going to list a few signs which can be linked to spy software on your phone. It's important to know that some of these signs can be caused by other things.
Perhaps you know about another child that you don't want your child to contact. Or there could be someone she is contacting who is a stranger to you. You need to know who your child is contacting in order to protect them. Mobile Spy logs all contacts that are saved on the mobile phone. User cannot block the certain content from the web that proves to be a failure in controlling the behavior of kids online.
The SpyEra is active in monitoring on-goings on target device. User may find little inconvenience in the customer support service as contact numbers of any responsible authority is not available but email services compensate it. AppMia is a perfect cell phone monitoring software. It offers free upgrades, affordable price and lives customer support, no jailbreak, one time license and many more.
AppMia however does not offer free version for trial and only the reviews about AppMia can help you in making the decision of its purchase. It is good for regular use and has a customer page where information is presented in accessible manner. The page is accessible from any device. People who have used the basic version said that it lack some of the features which is only presented in the premium version. The premium version is a bit expensive. The features of AppMia are quite good and useful, but it is not recommended for the professional use. So, these are the top 10 mobile spy apps or software of Interested users can buy according to their needs and budget.
All the applications are capable of catering the spying need at their best. The difference comes only in the pricing and features that they offer. Some offer good and affordable pricing of packages but lack in the features while others lack in providing the free version.
So, undoubtedly the user can blindly trust on the best among them, and that is TheTruthSpy. We are not encouraging you to decide without having a solid reason. The reviews of this app itself show that the app is worthy and they rely on TheTruthSpy without any worries. TheTruthSpy offers some incredible features that will make you believe that the app works exceptionally well.
Tracking the location is the very crucial step in monitoring the kids. Location can tell you so many things about the target person.
How Does Cell Phone Spy Software Work?
Monitor the location remotely and view their current location and details like latitude, longitude and street address. Turn on the GPS history function from the settings and check their history. Track the location for a specific duration when they go out by changing the default time. To view the position of the person click on the GPS history of the control panel. To track real-time location click on get GPS now. It let you know information about every step of the target person. Spy call and Ambient recording.
This feature of TheTruthSpy turns the device into the bugging device. It helps you hear the live surroundings. To use this feature, turn on the auto answer. Then set the mobile number to be monitored. The device will have no record of this call, and thus the user is safe. For the recording of the surrounding voice, click on start button at the control panel. The sound will be recorded in an MP4 file which user can download later. The feature allows you to hear for almost 20 minutes and by clicking again on the start button, you can listen for another 20 minutes.
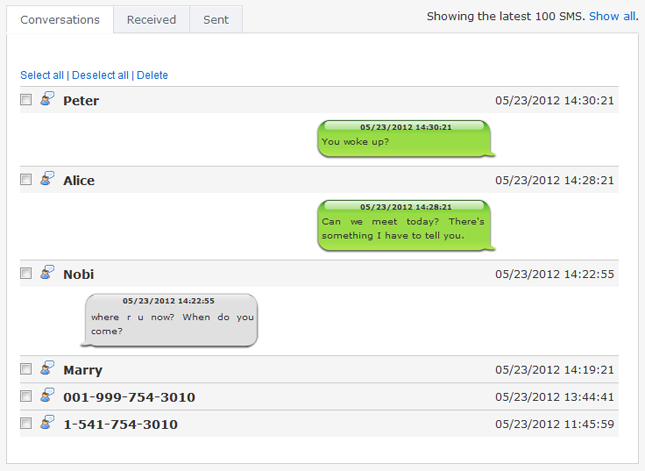
TheTruthSpy is smart to track the incoming and outgoing messages from the device where TheTruthSpy is installed. Reading the content of all new and older messages is very easy with this feature. Name and number of the recipients are informed to the user on their login page. The messages are accessible from any location and anytime within few seconds. TheTruthSpy is efficient in uploading the notes as soon as they are sent to the device.
It works quickly fast and makes no mistake in offering the useful information to the user of TheTruthSpy. It shows the latest message on the front page and to view the older messages click on show all option. The conversation is shown similarly you communicate with another person. Social media platform has become the central location to meet, and thus smartphone users stay active here most of the time. By staying in touch with their activities on social media TheTruthSpy user can get huge information. Therefore, it let you track the social media application like WhatsApp, Facebook, Instagram and other popular apps.
Tracking messages here are very important in comparison with tracking of text messages. TheTruthSpy reveals every activity on this platform. As these applications also allow making free calls, both voice and video, therefore, TheTruthSpy is efficient to track all such activities. Truthspy can record every key pressed on the device of your kids, employees or other. The feature helps the user in knowing the password of other apps installed on the device or tracking of Facebook and another password. The US Federal Trade Commission has sued Internet marketing organizations under the " unfairness doctrine " [74] to make them stop infecting consumers' PCs with spyware.
In one case, that against Seismic Entertainment Productions, the FTC accused the defendants of developing a program that seized control of PCs nationwide, infected them with spyware and other malicious software, bombarded them with a barrage of pop-up advertising for Seismic's clients, exposed the PCs to security risks, and caused them to malfunction.
Seismic then offered to sell the victims an "antispyware" program to fix the computers, and stop the popups and other problems that Seismic had caused. The case is still in its preliminary stages. It applied fines in total value of Euro 1,, for infecting 22 million computers. The spyware concerned is called DollarRevenue. The law articles that have been violated are art. The hijacking of Web advertisements has also led to litigation. In June , a number of large Web publishers sued Claria for replacing advertisements, but settled out of court. Courts have not yet had to decide whether advertisers can be held liable for spyware that displays their ads.
In many cases, the companies whose advertisements appear in spyware pop-ups do not directly do business with the spyware firm.
Rather, they have contracted with an advertising agency , which in turn contracts with an online subcontractor who gets paid by the number of "impressions" or appearances of the advertisement. Some major firms such as Dell Computer and Mercedes-Benz have sacked advertising agencies that have run their ads in spyware. Litigation has gone both ways. Since "spyware" has become a common pejorative , some makers have filed libel and defamation actions when their products have been so described. In , Gator now known as Claria filed suit against the website PC Pitstop for describing its program as "spyware".
In the WebcamGate case, plaintiffs charged two suburban Philadelphia high schools secretly spied on students by surreptitiously and remotely activating webcams embedded in school-issued laptops the students were using at home, and therefore infringed on their privacy rights. The school loaded each student's computer with LANrev 's remote activation tracking software. This included the now-discontinued "TheftTrack". While TheftTrack was not enabled by default on the software, the program allowed the school district to elect to activate it, and to choose which of the TheftTrack surveillance options the school wanted to enable.
TheftTrack allowed school district employees to secretly remotely activate the webcam embedded in the student's laptop, above the laptop's screen.
Web-Based Control Panel
That allowed school officials to secretly take photos through the webcam, of whatever was in front of it and in its line of sight, and send the photos to the school's server. The LANrev software disabled the webcams for all other uses e. In addition to webcam surveillance, TheftTrack allowed school officials to take screenshots, and send them to the school's server.
In addition, LANrev allowed school officials to take snapshots of instant messages, web browsing, music playlists, and written compositions. The schools admitted to secretly snapping over 66, webshots and screenshots , including webcam shots of students in their bedrooms. From Wikipedia, the free encyclopedia. This article has multiple issues. Please help improve it or discuss these issues on the talk page.
Learn how and when to remove these template messages. This article may be in need of reorganization to comply with Wikipedia's layout guidelines. Please help by editing the article to make improvements to the overall structure. November Learn how and when to remove this template message. This article's lead section may be too long for the length of the article.
Please help by moving some material from it into the body of the article. Please read the layout guide and lead section guidelines to ensure the section will still be inclusive of all essential details. Please discuss this issue on the article's talk page.
This section does not cite any sources. Please help improve this section by adding citations to reliable sources. Unsourced material may be challenged and removed. December Learn how and when to remove this template message. List of rogue security software , List of fake anti-spyware programs , and Rogue software. Lower Merion School District. Archived from the original PDF on November 1, Retrieved March 7, Retrieved November 28, Archived from the original on February 27, Retrieved April 10, Web Browser security vs.
Why Cornell Did It".
Archived from the original on February 14, Cornell University, Office of Information Technologies. Archived from the original on November 3, Retrieved July 27, Retrieved November 14, Massive spyware-based identity theft ring uncovered. Ars Technica, August 5, The Legacy Sunbelt Software Blog.
Federal Trade Commission, September 3, Retrieved November 22, Retrieved November 29, Retrieved June 13, Retrieved August 31, Archived from the original on November 19, Retrieved November 21, Archived from the original on January 6, Retrieved September 4, The New York Times. Archived from the original on May 9, Retrieved September 11, Washington State Office of the Attorney General.
Retrieved 20 November Archived July 15, , at the Wayback Machine.

June 25, Archived November 3, , at the Wayback Machine. Archived September 29, , at the Wayback Machine.
- sport tracker windows phone 8.
- What Is Spyware and Spying Software Functions.
- What is Spy Software??
- spy iphone 7 software.
- spyware for iphone 7 review.
Archived from the original on February 6, Sunbelt Malware Research Labs. It is possible that this spyware is distributed with the adware bundler WildTangent or from a threat included in that bundler. Archived May 5, , at the Wayback Machine. Archived from the original on March 23, Archived from the original on May 10, Retrieved July 10, Fake antivirus is 15 percent of all malware".